Ransomware Readiness Assessment
Overview
- Prepare your organization for ransomware threats
- Discover if your security controls can safeguard your data from ransomware
- Evaluation of your organization’s current people, processes, and technology, while simulating adversary tactics, techniques, and procedures (TTPs) in your environment.
- Comprehensive security strategy to prepare for a ransomware attack, prevent compromise of systems, protect and isolate critical data, and enhance enterprise response capabilities
Top Outcomes & Benefits
- Maturity – Identify key weaknesses and strengths in ransomware defense capabilities and controls.
- Recover Faster – Improve Incident Response. Minimize downtime. Restore to most recent clean state with just a few clicks.
- Operational Efficiency - Recognize deficiencies in the management of ransomware tasks
- Strategy – Prioritized highly actionable recommendations to further strengthen your readiness and guidance to mitigate future ransomware attacks
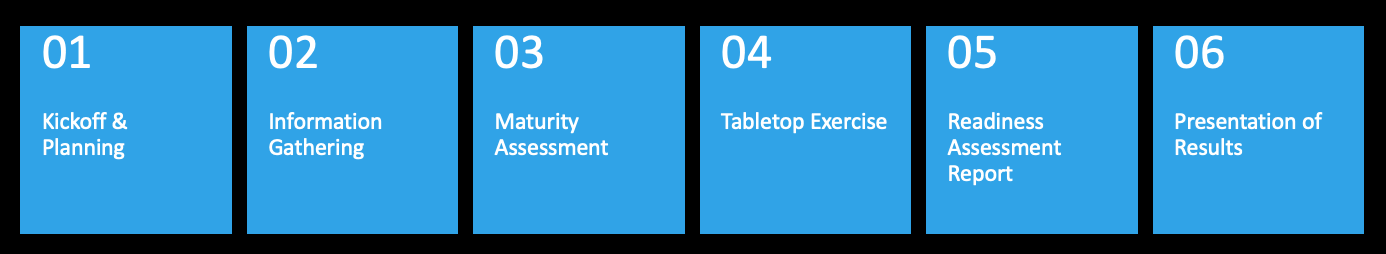
Base Tier Methodology
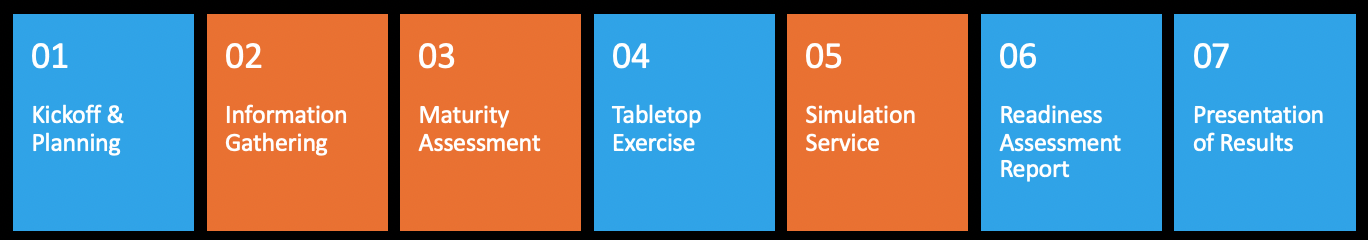
Premier Tier Methodology
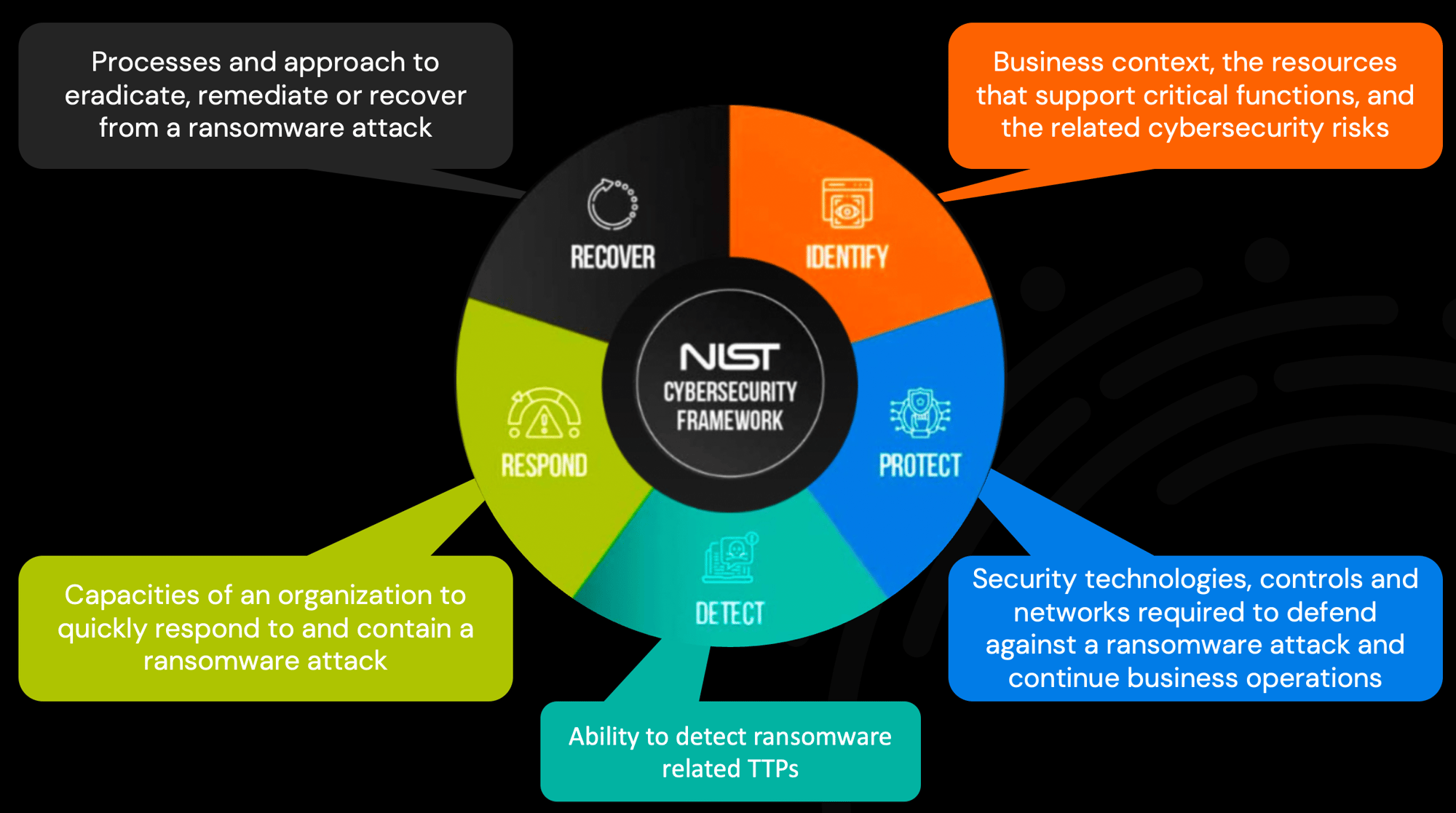
Focus Areas
Examples of Areas Evaluated
- Backup process assessment including backup of data on systems (desktop and laptops), servers, and critical configuration files
- Business Continuity – BCP testing and evidence of testing
- Disaster recovery planning and proof of a working DR plan
- Malware and Ransomware detection and quarantine capabilities review
- Network and firewall assessment, including traffic monitoring
- Event monitoring – server and endpoint
- Endpoint security and encryption assessment, including response solutions
- User training on ransomware
- Incident response processes, tools, and plan review
Table Top Exercise
- Working through mock scenarios to identify gaps and test your people, processes, and technology
- Validate that ransomware response procedures will work
- Verify processes into Playbooks
- Conducted in a highly engaging and interactive format, our Ransomware Tabletop Exercises ensure maximum participation and highly relevant output, and constructive discussions
- Confirm communication processes upon learning of the attack
- Verify that essential systems, applications, files, databases and other resources are protected
- Deliverable: Objective analysis of the exercise and provide a formal document which includes response plan gaps and shortfalls
Ransomware Incident Simulation
- Simulate lateral movement using common Ransomware techniques
- Simulation starts from one or multiple machines
- Test segmentation between networks to determine if ransomware can spread to other environments, such as:
- Manufacturing and plant (OT) networks
- Backup infrastructure networks
- Retail networks
- Other secure networks
- Test for accessible file shares which could be accessed by ransomware
- Simulate ransomware encryption behavior by using a custom, non-destructive ransomware emulation tool to mimic file encryption
- Review organization’s response capabilities
- Emulates real Tactics, Techniques, & Procedures (TTP)
- Mapped to MITRE ATT&CKTM
- Supports all types of networks and workloads: containers, public and private clouds