Zero Trust Access to Git - Configuring Cisco Duo & GitHub Enterprise
Source code repositories can be the crown jewels of many organizations. For this and many other reasons, it is a higher ...
Source code repositories can be the crown jewels of many organizations. For this and many other reasons, it is a higher risk target for adversaries and modern cyber threats. In this configuration example, we will integrate Cisco Secure Access by Duo and GitHub Enterprise to apply Zero Trust policies.
Applying zero trust policies to SaaS solutions typically involves integrating the application via SAML, OIDC, etc. One of my favorite guides on SAML is on the Duo Blog: The Beer Drinker’s Guide to SAML.
|
TIP If your application is on-premise or doesn't support modern authentication. Zero Trust Network Access(ZTNA) and the Duo Network Gateway(DNG) Allows organizations to perform the same exact user and device trust checks on legacy applications and services. |
Integrating Github Enterprise with Duo via SAML
Step 1: Navigating to GitHub Authentication Settings
To get started, login to your GitHub account and...
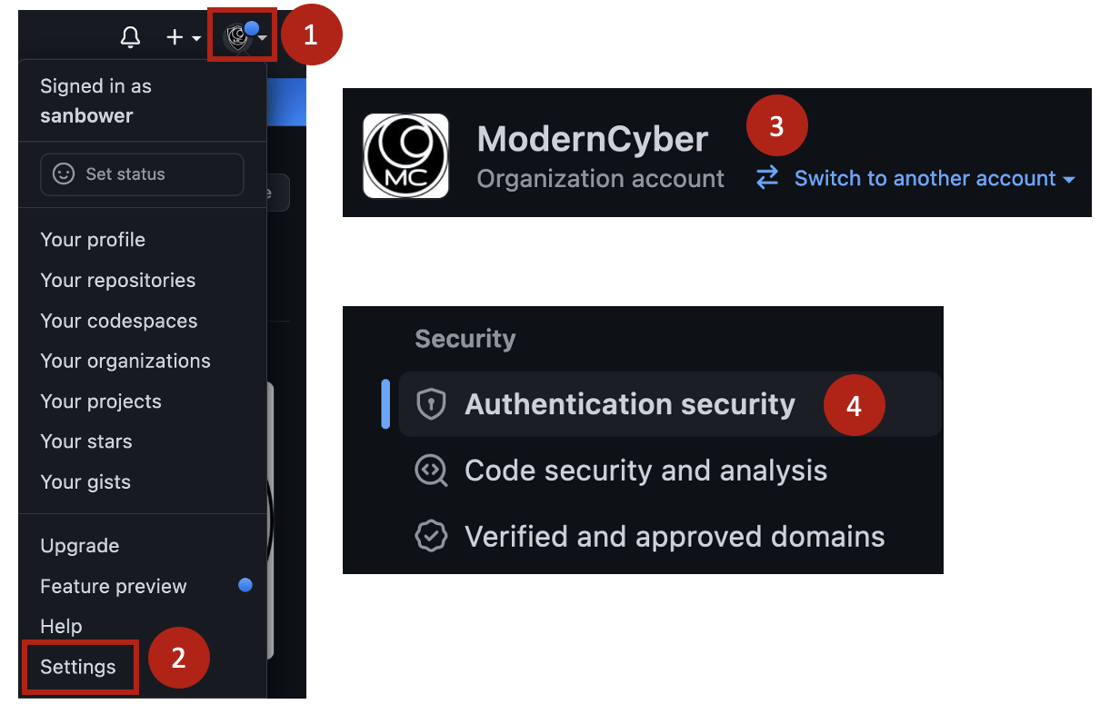
- Click your Avatar in the top right of the GitHub UI
- Select Settings
- Switch to your organization's account
- Select Authentication security in the left menu
|
NOTE
You need to be an organization owner to have the correct rights and permissions to enable SSO/MFA/SAML for an Organization |
Step 2: Enable SAML Authentication on your GitHub Organization
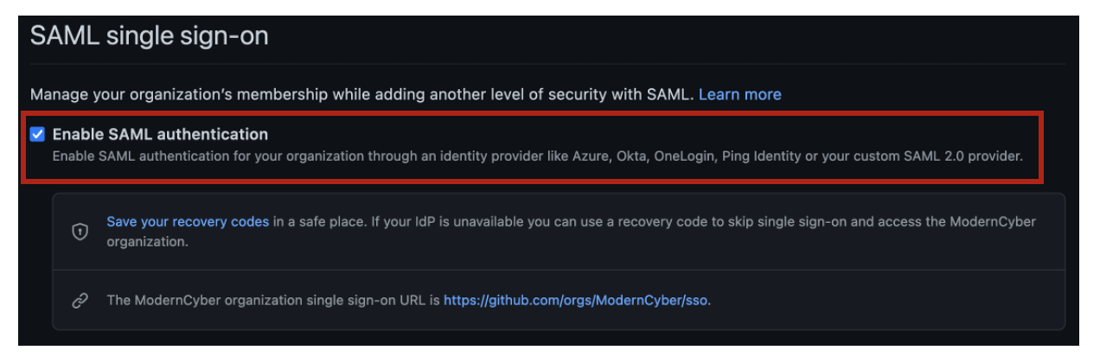
Next, check the box to Enable SAML authentication
Step 3: Add a new Generic SAML Application in Cisco Duo
Next, login to your Duo account and perform the following steps to add an application for GitHub integration.
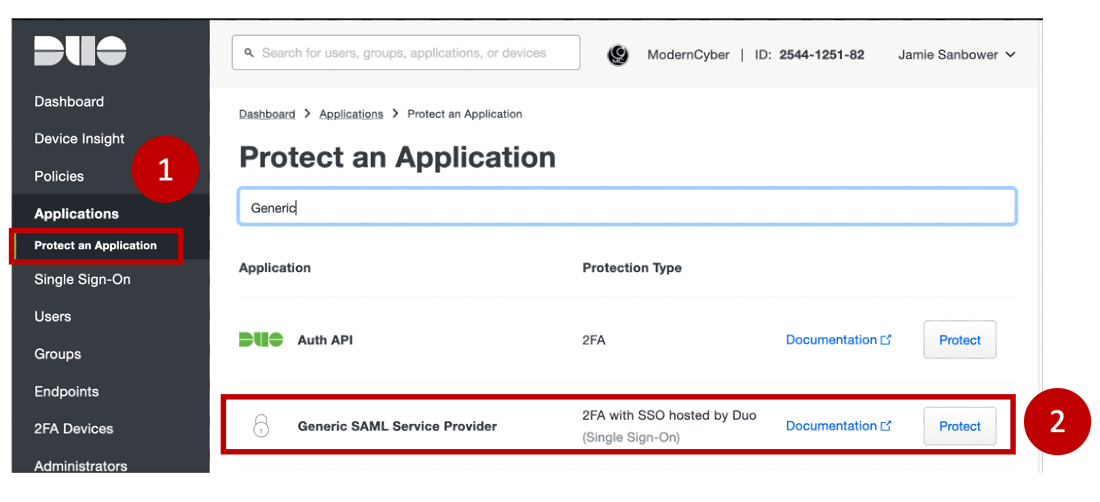
- Select Protect an Application
- Search and Select Generic SAML Service Provider
Step 4: Duo -> Github Configuration
Next, Copy configuration details from Cisco Duo and input them into SAML Configuration in Github
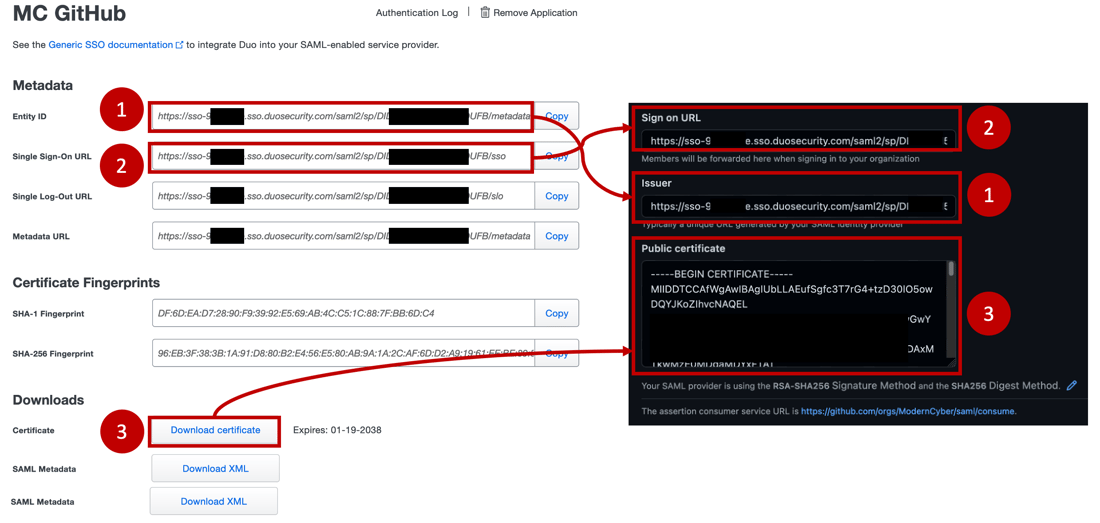
- Copy the Duo Entity ID and paste it as GitHub's Issuer
- Copy the Duo Single Sign-On URL and paste it as the GitHub's Sign-on URL
- Click Duo's Download Certificate button, open the certificate in your favorite text editor, and paste it as GitHub's Public certificate
Step 5: GitHub -> Duo Configuration
Next, Copy configuration details from GitHub's SAML Configuration and input them into Cisco Duo's application configuration
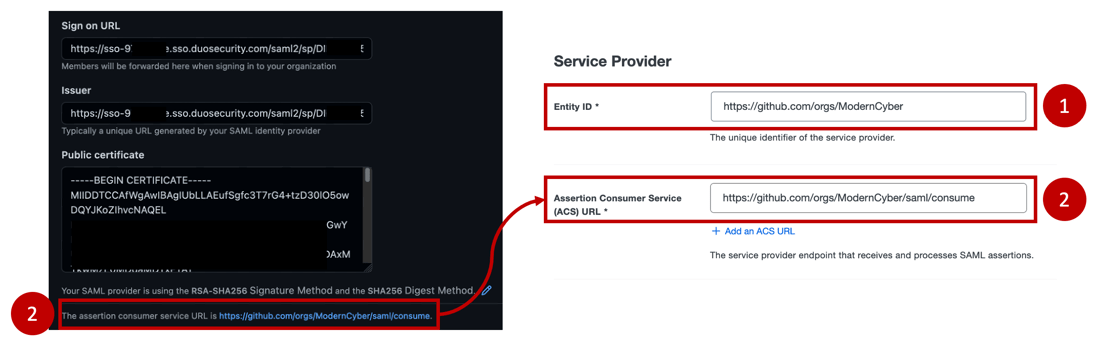
- Under the Duo Service Provider configuration input your organization URL (typically github.com / orgs / <Organization Name > ) as the Entity ID
- Copy the GitHub assertion consumer service URL and paste it as the Duo Assertion Consumer Service (ACS) URL
- Scroll to the bottom of the page and save the configuration in the Duo Admin session.
Step 6: Test the Integration
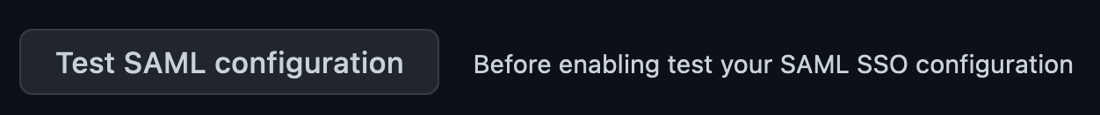
Next, click the Test SAML configuration button on your GitHub page.

|
CAUTION If your test does NOT succeed, do NOT proceed or click Save as this could lock you out of your organization. |
Step 7: Require SAML SSO
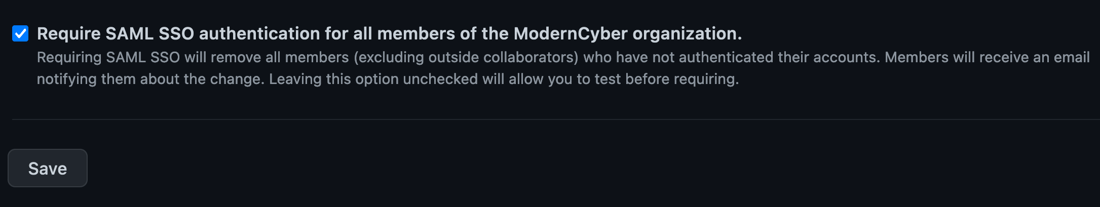
Finally, check the box to Require SAML SSO authentication for all members of your organization and then click Save.
Zero Trust Policies for GitHub Application Access
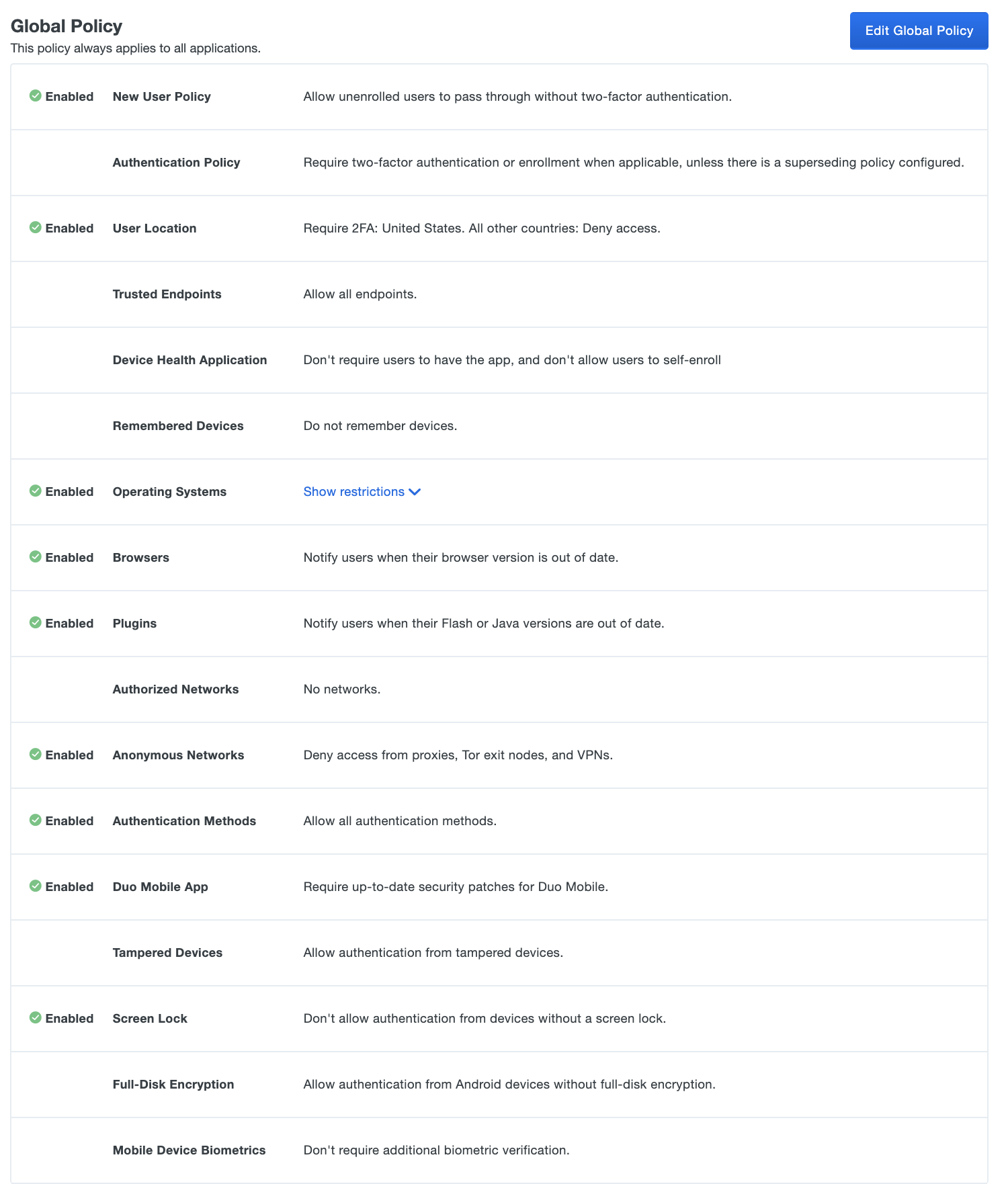
By integrating GitHub with Duo, you now can use Duo's Adaptive Policy & Control to meet your organization's requirements around zero trust and move your Zero Trust Maturity to optimal for Identity. A few of the top policy items:
Risk-Based Authentication
Risk-Based Authentication is the difference between advanced and optimal zero trust maturity.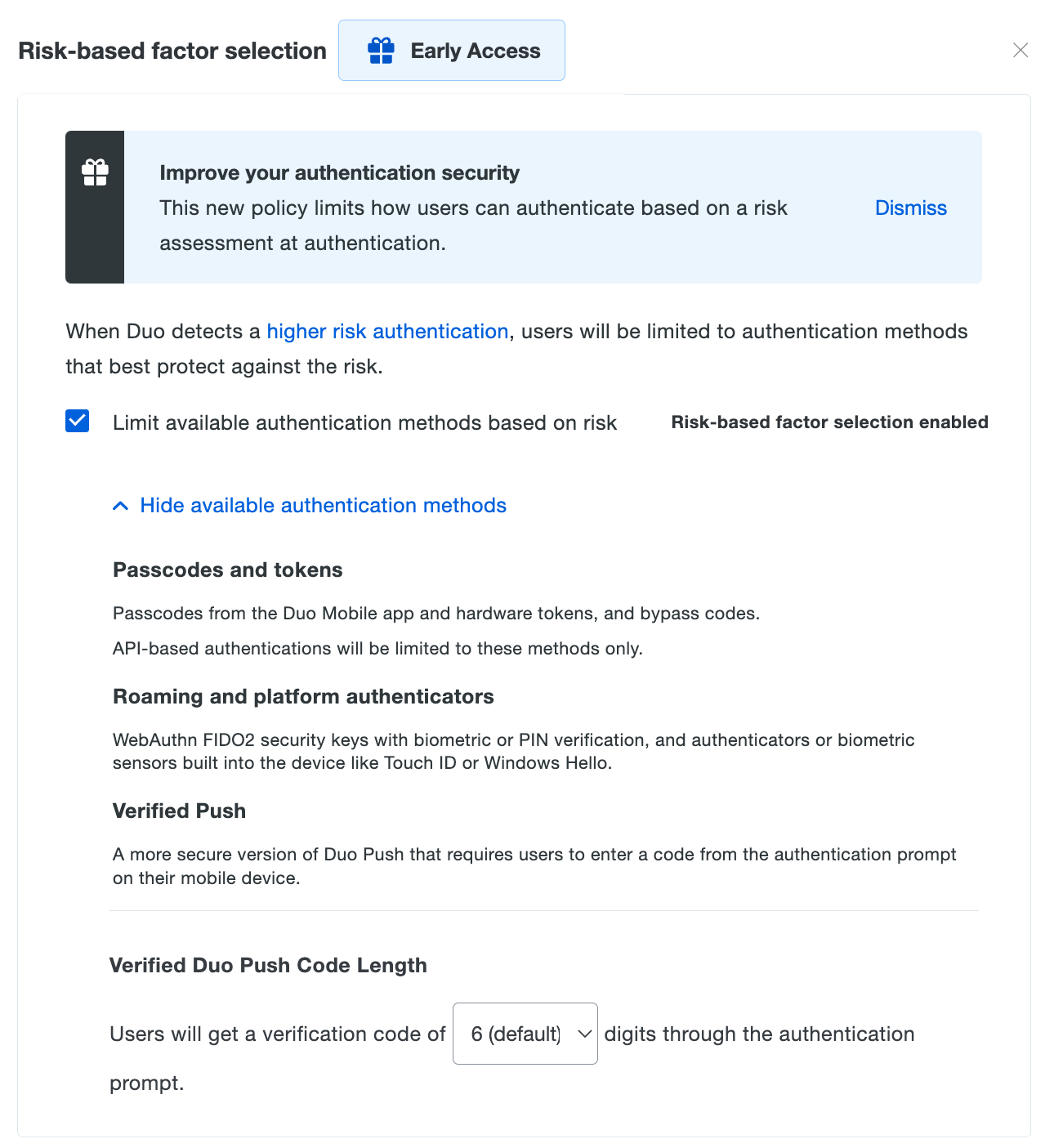
Managed Device Check
Duo integrates with your favorite endpoint and mobile device management tools to determine if the device is managed and trusted.
Duo Device Health
Duo Device Health allows organizations to control access to your applications through the policy system by restricting access when devices do not meet particular security requirements.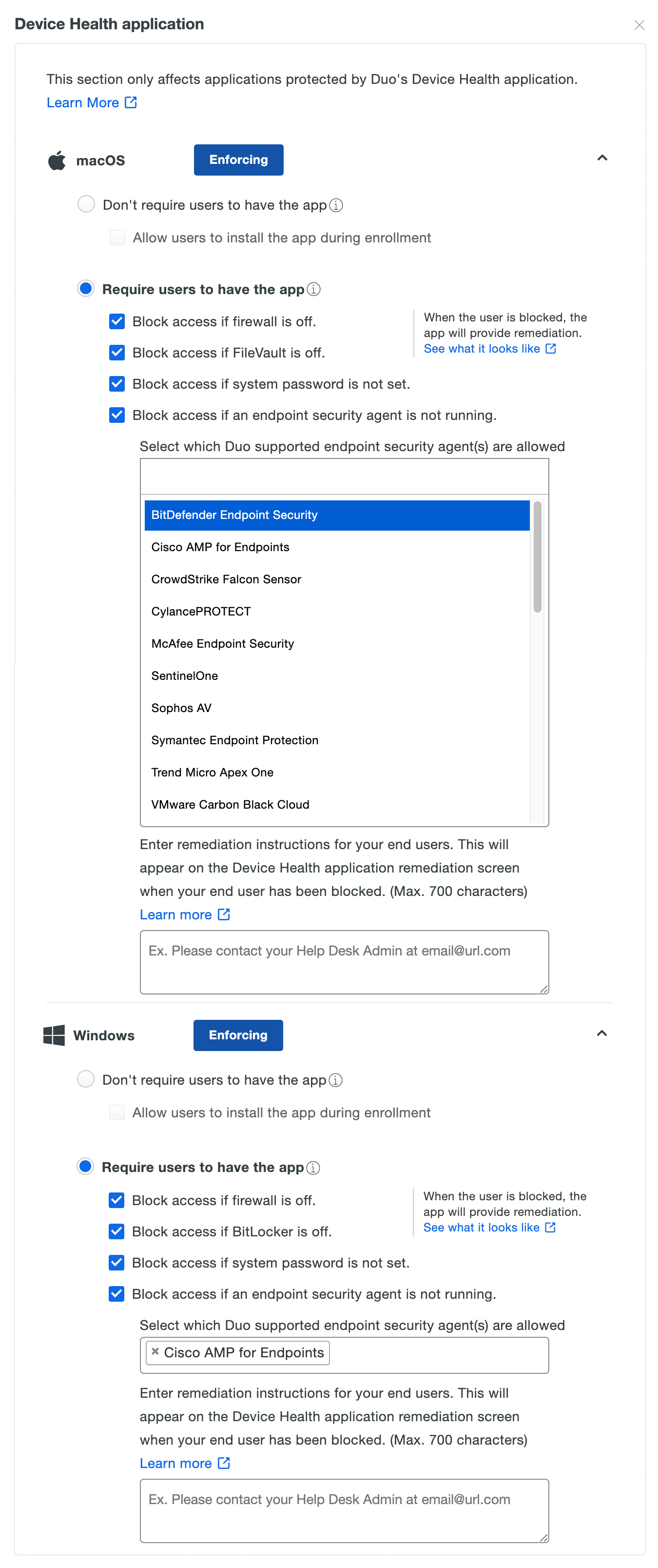
Getting Help
If you are looking for help with Cisco Duo, MFA, SSO, Zero Trust, etc. Schedule some time to speak with one of our cybersecurity experts.