The Role of Zero Trust in Ransomware Defense
Ransomware has made headlines for many years, because of its notorious reputation for business disruption, shutting ...
Ransomware has made headlines for many years, because of its notorious reputation for business disruption, shutting down critical infrastructure (Colonial Pipeline Paid Hackers Nearly $5 Million in Ransom), and even death (Ransomware attack might have caused another death). From Ransomware for Dummies: Ransomware is malicious software (malware) used in a cyberattack to encrypt the victim’s data with an encryption key that is known only to the attacker, thereby rendering the data unusable until a ransom payment (usually a cryptocurrency, such as Bitcoin) is made by the victim.
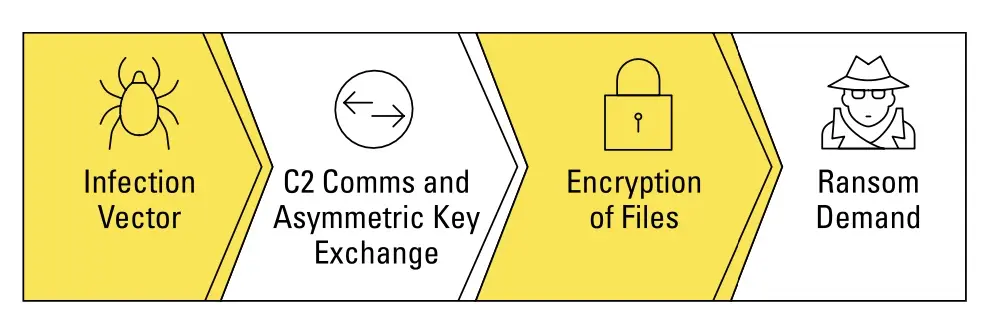
Ransomware is commonly delivered through exploit kits, waterhole attacks (in which one or more websites that an organization frequently visits are infected with malware), malvertising (malicious advertising), or email phishing campaigns (see Figure 1).
Unfortunately, there are no signs of bad actors slowing down(Ransomware Attacks Are Spiking. Is Your Company Prepared?) and why would they, when the payouts are only increasing:
2019 Ransomware Stats
- Two-thirds of ransomware attacks targeted state and local governments. (source)
- Over 500 US schools were affected by ransomware attacks in 2019. (source)
- Nearly 70 US government organizations were infected by ransomware since January 2019. (source)
- A total of 140 US local governments, police stations, and hospitals have been infected with ransomware.
2020 Ransomware Stats
- 51% of businesses were targeted by ransomware. (source)
- By the end of 2020, ransomware costs reached $20 billion for all businesses. (source)
- The average ransomware payout demand was $233,817 in Q3 2020. (source)
- 1 in 5 SMBs and 4 in 5 MSPs were targeted by ransomware attacks. (source)
2021 Ransomware Stats
- 37% of IT organizations across 30 countries were hit by ransomware in the last year. (source)
- From Jan 1 - May 25, 82 ransomware attacks targeted the healthcare sector alone. (source)
- The average mitigation cost of a ransomware attack was $1.85 million. (source)
- Companies experience 21 days of downtime on average following a ransomware attack. (source)
- 80% of victims who gave into ransom payouts experienced another attack soon thereafter. (source)
A Real Life Case Study
Most organizations have invested in the right security technology and put into place many controls to minimize risk, but is it enough? One of the best examples, of the devastating effect of ransomware, is NotPetya. In minutes, NotPetya:
- Spread to all end-user devices, including 49,000 laptops
- All 147 Active Directory Servers ceased to exist
- Brought down 1,200 applications
- ~1,000 applications were destroyed.
- Backups were unusable
- Around 3,500 servers were destroyed
- All fixed-line phones were inoperable due to the network outage
- Mobile Devices were synchronized with Outlook, all contacts had been wiped— severely hampering any kind of coordinated response.
It doesn't matter how fast you type or what your incident response plan contains, ransomware is just as fast or faster at destruction.
Mitigating Ransomware with Zero Trust
Completely preventing ransomware infection is almost impossible. However, organizations can minimize their attack surface and limit the blast radius, in effect, limiting their ability to find the path of least resistance and quickly move across a compromised network. While there’s no panacea to stopping a ransomware attack from occurring, implementing a zero trust architecture enables organizations to contain the damage of an attack, limiting the extent to which an incident can cause damage and the impact of refusing to pay the ransom. Reducing the scope and impact of a ransomware attack is where zero trust excels. In order to understand how zero trust architecture is critical in a ransomware defense strategy, you must go a little deeper into the attack kill chain of ransomware. Microsoft describes the lateral movement and the attack chain in an article:
Attackers move laterally to escalate privileges or to steal information from specific machines in a compromised network. Lateral movement typically involves adversaries attempting to co-opt legitimate management and business operation capabilities, including applications such as Server Message Block (SMB), Windows Management Instrumentation (WMI), Windows Remote Management (WinRM), and Remote Desktop Protocol (RDP). Attackers targeft these technologies that have legitimate uses in maintaining functionality of a network because they provide ample opportunities to blend in with large volumes of expected telemetry and provide paths to their objectives. More recently, we have observed attackers performing lateral movement, and then using the aforementioned WMI or SMB to deploy ransomware or data-wiping malware to multiple target machines in the network.
A recent attack from the PARINACOTA group, known for human-operated attacks that deploy the Wadhrama ransomware, is notable for its use of multiple methods for lateral movement. After gaining initial access to an internet-facing server via RDP brute force, the attackers searched for additional vulnerable machines in the network by scanning on ports 3389 (RDP), 445 (SMB), and 22 (SSH).
The adversaries downloaded and used Hydra to brute force targets via SMB and SSH. In addition, they used credentials that they stole through credential dumping using Mimikatz to sign into multiple other server machines via Remote Desktop. On all additional machines they were able to access, the attackers performed mainly the same activities, dumping credentials and searching for valuable information.
Figure 2: PARINACOTA attack with multiple lateral movement methods
Most ransomware kill chains include some form of credential dumping or password attacks and lateral movement. Cisco Talos explores other examples, including the nefarious WannaCry, in their useful blog post: Back to Basics: Worm Defense in the Ransomware Age. Many of the recommendations align directly with ModernCyber's Zero Trust Principals:
- Remove Implicit Trust
- Enforce Risk-Based Least Privilege
- Assume Compromise
In the example of WannaCry, along with limiting the lateral movement, an organization would've highly benefited from blocking connections to TOR nodes and TOR traffic on their networks. No matter what your college intern tells you, TOR is not something typically utilized across any industry (Manufacturing, Healthcare, Financial, Education, Government, etc.). If the organization were enforcing risk-based least privilege, Tor, a high-risk, low-business-relevant application, would be denied. Even if your organization has a researcher or research group that needs tor for their mission or goals, in a least privileged model, the policy would only allow the limited usage of the application. In May of 2021, President Biden signed an executive order, in response to the number of incidents and damage caused by ransomware. The order calls on the Federal Government to take decisive steps to modernize its approach to cybersecurity including how they must advance toward Zero Trust Architecture:
In essence, a Zero Trust Architecture allows users full access but only to the bare minimum they need to perform their jobs. If a device is compromised, zero trust can ensure that the damage is contained. The Zero Trust Architecture security model assumes that a breach is inevitable or has likely already occurred, so it constantly limits access to only what is needed and looks for anomalous or malicious activity. Zero Trust Architecture embeds comprehensive security monitoring; granular risk-based access controls; and system security automation in a coordinated manner throughout all aspects of the infrastructure in order to focus on protecting data in real-time within a dynamic threat environment. This data-centric security model allows the concept of least-privileged access to be applied for every access decision, where the answers to the questions of who, what, when, where, and how are critical for appropriately allowing or denying access to resources based on the combination of sever.
Defense against the dark arts Ransomware with Zero Trust Capabilities
If you've read this far into the post, you probably don't already have a full zero trust architecture implemented yet and that is ok. While zero trust should be your strategic goal for cybersecurity, many don't realize that there are many practical and easy ways to start introducing zero trust principals into your organization. Figure 3 illustrates the Practical Ways to Reduce Ransomware Impact and some of the security controls and technologies to apply.

While, these are not directly aligned to zero trust they all can be implemented using zero trust principals. Honestly, there are hundreds, if not thousands of secuirty technologies and controls that help overall with ransomware, but to help focus efforts, here are ModernCyber's top 5 zero trust capabilties that can make an impact in reducing the risk of ransomware:
- Microsegmentation
- Multi-Factor Authentication (MFA)
- Cyber Hygiene
- Remove Implicit Trust
- Automated Threat Response
Microsegementation
While enforcing risk-based least privilege is the ultimate goal, it is much easier to implement explicit deny access control lists (ACLs) to stop lateral movement. The key requirement is to ensure you are able to enforce the policy between devices that could be on the same physical or virtual network (east-west segmentation). Whether it is 2 workloads in the subnet or two laptops on the same access point (AP), the best place to start is by blocking the most common protocols and ports used for ransomware propagation. These include MS-SMB (TCP Port 445), MS-RPC and WMI (TCP Port 135), PowerShell Remote (TCP Port 5985-5986), RDP (TCP Port 3389), SSH (TCP Port 22).
Multi-Factor Authentication (MFA)
A majority of breaches involved compromised credentials. MFA can be deployed rapidly and integrated with existing access methods and applications to ensure ransomware can't use that password to cause havoc. Don't forget about the machine and local accounts on devices. While not everything supports MFA, a unique strong password per device should be used to reduce the risk of credential dumping & brute force attacks.
Cyber Hygiene
Start by using asset discovery and visibility to inventory the protected surface and understand the security posture of each device. Establish device trust and consistently enforce posture policies before access to networks, applications, or data, i.e. up-to-date security tools, encryption-at-rest, etc. Patch vulnerabilities quickly by automating and optimizing patch management. Ensure proper controls for primary infection points: email, web & rdp. Implement a backup and recovery plan including write once read many (WORM) storage and TEST!
Remove Implicit Trust
Stop implicitly trusting new applications or communications on devices or networks. Default deny statements in your firewalls, web security, security groups, etc., should be used for both inbound and outbound policies. Yes, that means turning off outbound ICMP traffic from all devices and quit allowing outbound email and DNS requests. Use a network analytics tool to audit traffic patterns, with the eventual goal of orchestration of least privilege policy. On endpoints & workloads, implement application whitelisting. In the cloud, use least privilege IAM policies!
Automated Threat Response
Ensure when the indicators of ransomware occur, such as command and control communications or internal scanning, Security Orchestration, Automation, and Response (SOAR) can programmatically contain the source of the incident. Containment or revoking trusted access, can be done via network segmentation, Identity & Access Management (IAM) attributes, or via dynamic policies.
Irregardless of your zero trust strategy, maturity, or architecture, the top 5 tactical zero trust capabilities can be used to immediately start reducing the risk of ransomware and other threats too!
Summary
With no doubts about the benefits of zero trust in the defense against ransomware, it should be a question of ""when"" and ""how"" your organization will implement the zero trust principals that minimize the risk and blast radius. Ensuring your zero trust journey has tactical milestones to minimize the impact of incidents or breaches should be a top priority. Least privilege could take years to become ubiquitous in your organization, but blocking the common communication used for lateral movement and reducing your attack surface can be done in days or weeks. Get in touch to discuss how to accelerate the time to value in your zero trust journey.
Take Away
Download a copy of our top 5 zero trust capabilities for ransomware defense infographic:

