Scaling ISE Deployments
Scaling Cisco Identity Services Engine (ISE) deployments is a critical aspect of network design. Underestimating the ...
Scaling Cisco Identity Services Engine (ISE) deployments is a critical aspect of network design. Underestimating the resources required can lead to performance bottlenecks, delayed authentication times, and even system failures. On the other hand, over-provisioning can result in unnecessary costs and underutilized resources.
The Cisco ISE team recently published a video sharing some best practices, common pitfalls, and strategies to ensure your ISE deployment is scaled accurately. I’d encourage you to watch the video in its full. In this blog post, I’ll highlight what I view as the key scaling tip that was shared.
Units not Endpoints

Suppose that you guesstimate that you have 25,000 endpoints in your network environment. It is tempting to look at a table like the one above and conclude that the correct solution for your deployment is a dedicated PSN on a Cisco SNS 3615.
But note that the Cisco ISE Scaling Guideline, which can be found here, bases its recommendations for the maximum concurrent active sessions ISE appliances can support on the test criteria that endpoints are authenticating using dot1x in the range of 2 to 4 times per day.
Depending on the types of devices in your environment, as well as your use cases, this may not be realistic! It is therefore very possible that an IT Team will underestimate the resources they require for ISE.
Let’s explain.
Broadly speaking, from the perspective of ISE Scaling, there are three kinds of device categories: wired, wireless, and IoTs & Mobile Phones. The key insight from the presentation that I want to share with you is that wireless and IoTs & Mobile Phones should be presumed to consume larger resources on ISE than wired devices. A simple rule-of-thumb is to plan for 2x consumed resources for Wireless devices, and 4x consumed resources for IoTs & Mobile Phones (compared to wired devices).
Additionally, ISE’s posture service should be planned to consume 4x the amount of ISE resources as authentication.

Why is this?
In the case of wireless devices, the basic reason is that wireless devices (e.g., laptops) can be mobile. As wireless devices move around the campus, for example a laptop going from an office to a meeting room to a cafeteria, they connect to one AP after another. As they do so, reestablishing their sessions can trigger re-authentications to ISE.
The same can be said about Mobile Phones, but on a greater scale. Imagine college students biking or skateboarding around campus. As they ride by building after building, they can trigger new re-authentications to ISE with their phones.
With IoT devices, like cameras and printers, the issue is that they tend to turn ‘on’ and ‘off’ frequently. For example, Axis Cameras are configured to re-authenticate every minute, resulting in 1400 authentications per day! Additionally, they often lack a ‘back off’ mechanism, meaning they will keep trying to re-authenticate even if they repeatedly fail authentication.
Scaling your Deployment
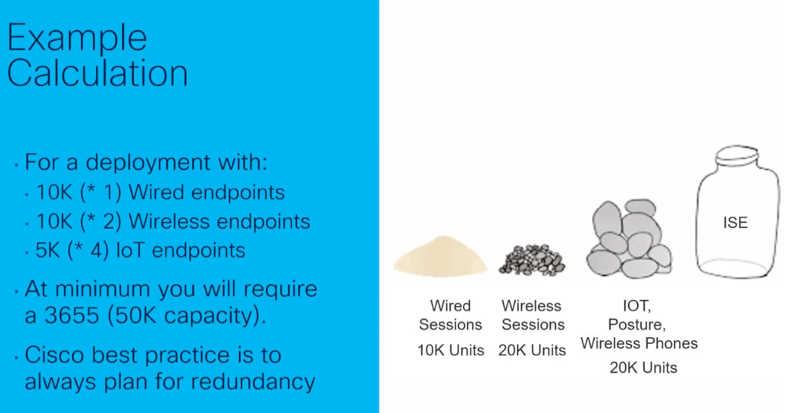
With these insights in mind, when it comes to scaling your ISE deployment, the key takeaway is to calculate each 1 wireless endpoint as 2 endpoints, and each 1 IoT or mobile phone as 4 endpoints. Also, don’t forget that the posture workflow consumes 4x as many units as authentication. So to return to the example we started with, depending on the type of 25,000 endpoints in your environment, instead of a SNS 3615 (25K capacity), you might actually need a SNS 3655, which supports 50,000 active sessions.
Deploying and configuring ISE can be challenging!
For more information on how ModernCyber can help to maximize your current ISE deployment, please check out some of our new offerings, such as our complimentary ISE Express Health Assessment as well as as our ISE Expert as a Service.