Line 'em Up
Have you ever had a package delivered to your house? I believe the answer would be a resounding "YES". Did you know how ...
Have you ever had a package delivered to your house? I believe the answer would be a resounding "YES". Did you know how many other packages were on the truck? How many miles that driver did that day, especially around the holidays? Do you know how much fuel was burnt to get that package to you? I can assure you that all the major shipping companies know exactly that and are always looking for ways to be more effective and efficient. In a 2017 article by CNN, it was reported that UPS found a way to save 10 million gallons of fuel, 6-8 miles per route, and drastically reduced the risk to the driver being injured in a vehicle accident. Your first guess may be that it was probably newer, safer electric or propane trucks. NOPE! The change was much simpler than that. All they did was change the process of their delivery routes by eliminating as many left turns as possible. Crazy, right? They changed a PROCESS without the need for new devices or capital expenditure.
We all likely know how many how many cyber threats we encountered today, or how many tickets those threats generated. Maybe that sparks the thought of, How can we assess our environment, much like UPS, to find a more effective and efficient way to combat the cyber threats we deal with daily? Effective cybersecurity has no shortage of best practices, due diligence, red tape, and processes that must be followed to achieve the desired risk protection for the corresponding threat tolerance and threat profile of the environment.
Through many discussions with customers around frameworks, mandates, and strategies such as National Institute of Standards and Technology (NIST) 800-207, Cybersecurity and Infrastructure Security Agency's (CISA) Zero Trust Maturity Model - Draft, the Executive Order (EO) on Improving the Nations Cyber Security and supporting Office of Management & Budget (OMB)Mandate M-22-09 we have come across a lot of instances where a process change similar to UPS could be all that is needed.
The first step that I recommend to many customers is to look at the capabilities they have in the environment already. I talked about this a bit in my last post "Avoiding Security Solution Tunnel Vision". With that out of the way, here we will build on that mindset and dig a little deeper. There is no silver bullet product to most of today's necessary responses to mandates and outcomes like Zero Trust. We need to take a more in-depth focus on security architectures over products or solutions. After breaking down capabilities, we need to get them "in line". What is this "line" you ask? Well, it's a process of understanding your business flows or communications that take place in your environment today. Whether you have clerks running credit card transactions through your point-of-sale systems, finance running numbers on payroll or PnL, or developers working on code for that next app or product that will launch the company into new markets. Understanding what the flows are within the environment is critical to applying security to those flows. Additionally, we should also identify where these capabilities fit into the framework or outcome we are trying to achieve.
For this example, we will use the Zero Trust pillars of User and Device Security, Network and Cloud Security, and Application and Data Security, as defined in the Cisco Zero Trust Architecture Guide.
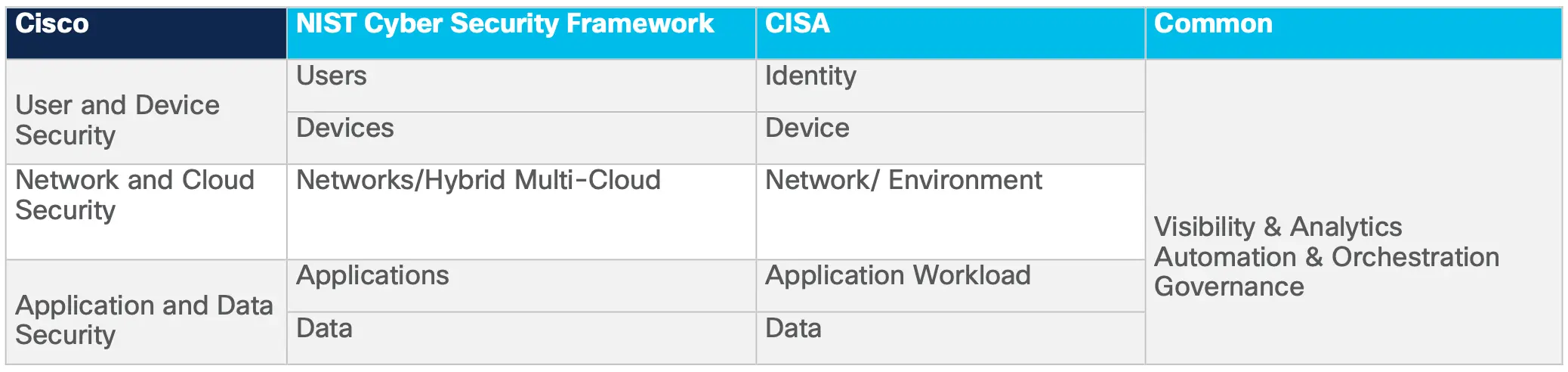
The next step, and sometimes the hardest, is understanding all the flows in the environment. In many cases this may be a monumental task but, I encourage you to take one bite at a time and maybe start with business-critical flows like the ones previously mentioned, Cisco SAFE Security Reference Architecture, or some from the Cisco Zero Trust Architecture Guide as shown in the example below.

An additional step that you may want to take is to also identify the common threats and risks associated with these flows. This step can help with identifying the capabilities you may want or need later in the process.

After you have a few flows in mind it is time to start getting your list of capabilities ready and identifying which capabilities you may need, want, or already have in those flows. This process again harkens back to my Tunnel Vision discussion where it is important to not think in the terms of products but capabilities. A list of capabilities can be found in the Zero Trust Architecture Guide and even in some cases right within the framework, or mandate you are trying to achieve. For example, we will use the Employee accessing a private application to drill down into the capabilities:

Once you have these flows with the capabilities you are at a key inflection point where identification of what you have vs. what you need can be clearly identified and noted for procurement, feature enablement, or even integration to start building your security architecture. Remember that it is not always a tool or solution to solve the problem, it may be as simple as changing a process. Another item that you may see highlighted here is the enforcement of policy may exist anywhere along the traffic path of those flows. There is no rule or statement that all enforcement must be done in a central data center or cloud security solution. The true value of an architecture and one of the goals of Zero Trust is for policy enforcement points to exist anywhere and everywhere no matter how the privileged user needs to access the systems or data.
Lastly, in our exercise, we can start to see your true mapping to models like CISA's Zero Trust Maturity Model and Zero Trust pillars by overlaying and sorting the capabilities into the pillars they support.

I know this may sound like an arduous process and maybe even untenable but, I can assure you that we have seen the wool come off the eyes of customers that did this exercise for only 3-5 business flows. They saw gaps that they didn't know existed, or overlapping tools and capabilities because the endpoint, network, and security teams all implemented their own solutions without looking at the entirety of the capabilities within the environment. Trust us, give it a try and you may see things that you didn't think about before or had no visibility to until working through the exercise.
Follow along for the next installment, as I am sure you have questions about how to stack, or use capabilities across multiple flows. We will cover that in the next blog. Also if you want to read ahead, take a look at Cisco Security SAFE Reference Architecture as it is the inspiration behind this methodology.
ModernCyber’s Assessment Services
If you are looking for guidance on top-of-mind outcomes like Zero Trust or Ransomware Readiness check out our services where we use this methodology to provide strategy, architecture, and technical implementation plans for success.
Schedule some time to speak with one of our cybersecurity experts.